Unveiling the Digital Cloak: The Art and Science of Cybersecurity Steganography
Introduction:
In the ever-evolving landscape of cybersecurity, staying one step ahead of potential threats is paramount. One technique that has gained prominence for its ability to enhance digital security is Steganography. This innovative method allows for the covert communication and concealment of sensitive information within seemingly innocuous data or files. In this blog post, we'll delve into the world of steganography, exploring its various types and essential criteria for success.
What is Steganography?
Steganography is the practice of concealing information within another message or physical object to avoid detection. Steganography can be used to hide virtually any type of digital content, including text, image, video, or audio content. That hidden data is then extracted at its destination.
Understanding Steganography:
Unlike traditional cryptography, which involves data encryption to protect it from unauthorized access, steganography takes a different approach. It focuses on hiding the very existence of confidential information within a host signal, making it an invaluable tool for both cybercriminals and cybersecurity professionals.
Types of Steganography:
Video Steganography: Leveraging digital video formats like MP4 and AVI to hide information within videos, employing techniques such as discrete cosine transform (DCT) for imperceptible data embedding.
Audio Steganography: With the increasing demand for Voice Over Internet Protocol (VOIP), audio steganography has become crucial. It involves concealing information within digital audio formats like WAVE and MPEG.
Network Steganography: Concealing data within network protocols such as UDP and ICMP allows for covert communication over networks while evading detection.
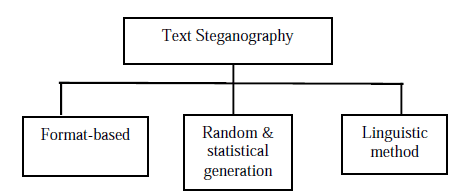
Text Steganography: This technique conceals information within text-based content, employing methods like capitalization, white spaces, and tab counts to hide data effectively.
Essential Criteria for Steganography Methods:
For steganography methods to be effective in enhancing digital security, they must adhere to specific criteria:
a) Accuracy: Steganographic techniques should guarantee reliable and precise data extraction from the host signal.
b) Volume: The capacity for embedding and concealing data within the carrier signal should be maximized.
c) Strength: Hidden data must be resilient, and capable of withstanding various processing actions without being compromised.
d) Privacy: Unauthorized disclosure of concealed data must be prevented, requiring password protection or encryption for authorized access.
In-Depth Look into Steganography Components...
Image Steganography Components:
Covered Image: Begin with an original image acting as a carrier for the hidden file.
Steganographic Image: Embed the hidden information inside the cover image, creating the steganographic image.
Message: Conceal the actual data within the steganographic image, which can be an image or plain text, depending on the chosen steganography technique.
Steganographic Key: To retrieve the message, use a steganographic key designed for the specific steganographic algorithm used.
Implanting Algorithm: Utilize an algorithm designed for hiding information inside the image while maintaining visual integrity.
Detaching Algorithm: For retrieval, employ a complementary algorithm, requiring the steganographic key to extract the hidden data.
Video Steganography Process:
Select a Cover Video: Choose a video file suitable for carrying the hidden message, ensuring it's of sufficient length and quality.
Prepare Your Message: Create the message or data you want to conceal within the video, whether it's text, an image, or other digital content.
Choose a Steganographic Algorithm: Select an appropriate algorithm for video files, such as those modifying video frames or pixel values.
Embed Your Message: Employ the chosen algorithm to embed your message within the video discreetly.
Set a Steganographic Key: For security, create a steganographic key required for extracting the hidden message from the video.
Save the Steganographic Video: Save the video as the steganographic version, and keep the steganographic key secure for future access.
Audio Steganography Steps:
Audio Carrier: Begin with an original audio file that will serve as a vessel for hiding secret data.
Steganographic Audio: Conceal the data within the audio carrier, creating steganographic audio that remains indistinguishable from the human ear.
Hidden Message: The concealed data can be text, audio clips, or other confidential information.
Steganographic Key: To extract the hidden data, use a steganographic key along with the extraction algorithm.
Embedding Algorithm: Employ specialized algorithms designed for hiding information within audio while preserving perceptual quality.
Extraction Algorithm: Retrieve the hidden data using the extraction algorithm in conjunction with the steganographic key.
Text Steganography Elements: Hiding in Plain texts.
Cover Text: Choose visible text that appears innocuous and acts as a carrier for the concealed message.
Steganographic Text: Conceal your information within the cover text, using techniques like letter casing, whitespace manipulation, or specific patterns.
Message: The confidential data concealed within the cover text can take various forms, such as plain text or encoded information.
Steganographic Key: Extract the hidden message using a steganographic key in conjunction with the extraction algorithm.
Embedding Algorithm: Utilize specialized algorithms for concealing data within text, ensuring that the changes remain imperceptible.
Extraction Algorithm: Decode and extract the concealed data using the extraction algorithm and the steganographic key.
Network Steganography:
Carrier Protocol: In Network Steganography, existing network protocols become carriers for concealed information.
Steganographic Payload: Embed hidden data within the carrier protocol, creating a steganographic payload that blends seamlessly with regular network traffic.
Secret Message: Concealed data can be text, files, or commands, hidden within the network traffic.
Extraction Key: Extract hidden data using a decryption key or extraction algorithm, ensuring authorized access only.
Insertion Technique: Discreetly insert secret data into the carrier protocol using specialized techniques and algorithms.
Extraction Process: Retrieve concealed information from network traffic using a complementary algorithm or key, preserving data privacy and confidentiality.
Conclusion
In the ever-evolving landscape of cybersecurity, Steganography emerges as a powerful ally for protecting sensitive data. Whether concealing messages within images, videos, audio, text, or network protocols, this technique provides an additional layer of security, making it challenging for unauthorized entities to detect or access confidential information. As the digital world continues to advance, Steganography remains a critical tool in the arsenal of data protection strategies.
To protect your digital assets effectively, consider employing Steganography as a means to safeguard sensitive information from prying eyes and potential threats.
Remember: While steganography can be a valuable tool for legitimate purposes, its misuse for malicious activities is illegal and unethical. Always use such techniques responsibly and within the bounds of the law.
Twitter Profile: https://x.com/Joyelhub23?t=o3etq7sHE4WrFabD18TZ5A&s=09








Comments